I think I've been hacked

| Discovering that you’ve been hacked is not a very pleasant experience. In fact, most people feel violated that a third-party with bad intentions has accessed their personal or business information and feel both personally responsible and professionally embarrassed. These feelings are totally natural and fully understandable |
| Our Secure Computer Healthcheck helps prevent future hacker access to your system and gives you peace of mind that your system is secure. | |
 |
Diagnose the root-cause of the hack and help you find out the initial vector of attack which hackers used to get into your computer or email account. |
 |
Manual examination of your system’s registry (Windows) or Plist files (Apple Mac) looking for suspicious entries which could be used to compromise your system even further. |
 |
Expert examination of your system’s program files or applications folder for malicious applications which may still be talking to the “command and control centre” of the hacker. |
 |
We manually examine the background processes running on your your Mac or PC operating system checking for unusual background processes which might bel compromising your data. |
 |
We examine your Windows or Apple OS X network logs to view any unusual connections that might still be active on your computer. |
 |
Expert examination of your system for viruses, spyware, keyloggers, worms or rootkits. This manual process detects malicious software which malware scanning software from the internet often misses. |
 |
Expert examination of your internet browser for any suspicious settings which might have been applied to it. For example, deliberate modification of DNS or proxy settings. |
 |
Removal of fake anti-virus, malware and other fake “security” applications which might be causing pop-up messages, browser re-directs or stealing data. |
 |
We expertly examine your system for remote login applications and remove them. |
 |
We disable built-in remote access for Apple and Windows. The prevents any bad actors having further access to your system. |
 |
We apply patches and updates to your Windows or Apple OS X operating system. |
 |
After hackers have stolen the login credentials for an email account, they will sometimes put them “up for sale” on the darkweb. We can check your email address and passwords against hacker databases on the darkweb. |
 |
We can professionally install and configure high-quality security software on your Windows or Mac system to help prevent your system from being compromised again. |
Telltale signs you’ve been hacked
- Friends or colleagues are informing you that they’re receiving suspicious or spammy emails from your email address. Some of them contain attachments.
- Friends or family members have contacted you to check if you’re really stuck in London, Paris or some other popular holiday destination after being robbed of all your money and credit cards.
- Your internet browser keeps on redirecting you to other websites or you keep seeing unwanted pop-ups on your screen.
- You receive pop-up warning messages on your computer screen saying that you have been infected with a virus. However, these look fake and do not look like they are from your operating system or computer security software.
- You receive a notification from your bank that your credit card has been compromised or start noticing suspicious entries on your bank or credit card statement.
- You are involved in a business or organisation and customers or members have said they have received an invoice from you demanding payment, but you never sent out these invoices.
- Customers have received an out-of-the-blue email from you that claims your bank account details have recently changed.
- Emails that you send using Gmail or Outlook 365 are getting rejected as spam.

I’ve been hacked. What actions should I take now?
- Do not panic. Try to access the potential damage calmly and objectively.
- Make sure that you’ve actually been hacked. Some users come to us assuming that, for example, their iCloud account has been hacked when, in fact, it is empty due to a glitch in their system.
- Disconnect all the infected devices from the internet as hackers may still have access to your device. This means disconnecting your ethernet cable from your PC or disabling the wireless or data connection on your phone.
- Reset all the passwords for online services, such as email, Dropbox, Facebook, Twitter and PayPal, and reset all the login details for online banking. This should be performed on a device which has NOT been compromised. If you reset passwords on a computing device still under the hacker’s control, the new passwords could be exfiltrated from your system by malware. Do not reuse any passwords or modify old ones. For example, changing your password from ‘liverp00l’ to ‘liverp00l2’ does not make it more secure! Ideally, use symbols, such as @!$?^, in your password.
- Contact friends, family and business associates to inform them that your email or social media accounts may have been compromised.
- Enable two-factor authentication (2FA) of your account. 2FA means that access to online accounts (such as email) will need both a password and another means of authentication, such as a swipe of a smartphone app to log in.
- Reset all of your answers to the security questions linked to that account. These questions would have been set up when you first opened your email account or possibly when you last modified your password and typically involve questions, such as what was your first car or who is your oldest cousin? Many IT security experts recommend that you deliberately lie when answering these questions to thwart any social engineering or open source intelligence attacks.
- Remove all third-party apps on your phone or tablet. This might sound like a rather drastic measure but there might still be a rogue app syphoning data from your phone. You can redownload these apps later. During reinstallation, they will need to be ‘reauthorised’. This process helps to filter out rogue apps.
How did I get hacked?
There are several ways that hackers may have infiltrated your computing device. Some possibilities include:
- You might have been phished. Phishing is a process whereby an attacker sends you a malware file (usually hidden in an attachment or web link) which once downloaded onto your computer system or smartphone can steal login credentials, such as usernames and passwords. These give the attacker free rein to login into your email, PayPal, iCloud, Google Drive, work network or even your online bank accounts. Some phishing scams involve the attacker sending you a payment request for a utility bill, such as gas, electricity or broadband, threatening imminent disconnection if it’s not paid immediately. The email will contain a link to a spoofed website where your credit card details get stolen. While a substantial number of phishing scams are international in nature, an increasingly large number of them are being localised to computer users in specific countries, such as Ireland. Such emails claim to be from organisations, such as Revenue Commissioners, Irish Water or Eir. Attackers sometimes target their phishing attacks at a specific audience, such as members of a specific profession or employees of a specific organisation.
- Your password used for email, online storage, etc. may have been brute-forced. This is where hackers use automated tools and databases of commonly used passwords to break into your account. Their systems ‘guess’ the password.
- A website or database where your email was stored has been hacked. Attackers can then use your email address to send you spoofed messages. It is important to NEVER use the same password for multiple websites. If you have reused the same email address/password combination, they can use this to hack into other online accounts.
- You clicked on a malvertising ad site. The site itself might be perfectly secure, but its advertising banners might be infected with malware. Even reputable sites, such as The New York Times and Yahoo have been the victims of malvertising.
- You might have downloaded an infected application or game. While games and applications might seem relatively benign, some of them can be conduits for nasty strains of malware that steal data, log keystrokes and steal passwords.
- You have been using a torrent site for downloading free movies, music or games. Unfortunately, these torrent sites or P2P sharing sites are magnets for viruses and malware.
- You gave away too much personal information on social media. Hackers have used the information that you posted on social media against you. Telling the world that you’ve just gone on holiday or just got a new job gives social engineers ample opportunity to exploit you.
How do hackers get access to all my contacts?
It is most likely they have done this by hijacking your PCs email application, your Gmail’s contact list or the contact list on your phone or tablet. Many apps, especially from the Android ecosystem, contain malware that steals contact information. These contacts can be used in future scams.
Please note: If you’ve lost access to your Gmail account, we cannot help you.
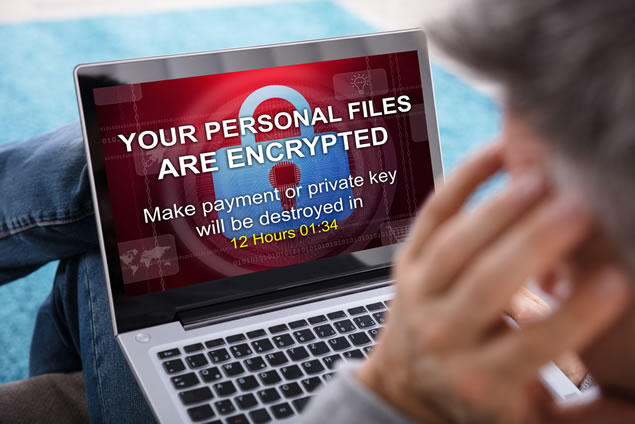
My computer has been infected with ‘ransomware’. Can you help?
Ransomware – the good news
If you’ve been infected with ransomware and think everything is lost – do not fret! Some users only get infected with ‘screenlocker’ software instead of full-blown ransomware. While this may give the appearance of ransomware, your files are not actually encrypted and are fully recoverable in most cases.
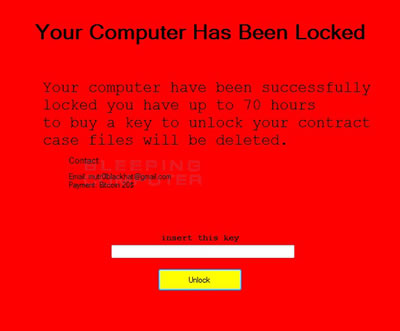
“Your Computer has been locked” – message from CryptoDevil screenlocker.
Ransomware – the bad news
Unfortunately, there is not much that can be done if your computer has been infected with ‘genuine’ ransomware, such as CryptoLocker, Teslascrypt, Wannacrypt or Locker. Most cryptoviruses and their variants use strong encryption algorithms, like RSA, which cannot be broken by using today’s technology.
Caveat Emptor – There are some software purveyors out there who claim their software can decrypt disks locked by cryptoviruses. Unfortunately, these do not work and they are the software equivalent of snake oil.

Locker ransomware screen
There are a small minority of cases where the attackers get sloppy and do not wholly encrypt your files but, in most cases, ransomware attacks are not recoverable.

I think my Facebook account has been hacked. What should I do now?
- Change your password immediately.
- Change your email account password also. Sometimes hackers “break into” a Facebook account by hacking someones email account first.
- Apple 2FA to our Facebook account.
- If your Facebook page has been cloned and is sending out friend requests – report it to Facebook as soon as possible. Report this using another channel other than Facebook messenger.
The Microsoft Support Scam (Fake Tech Support Scam)
Not all scams happen solely over the internet. A scam which has been doing the rounds for a number of years now is the ‘Microsoft Support Scam’ call. This is a ‘vishing’ scam where a ‘technical support agent’ telephones you, claiming to be from Microsoft, and informs you that you have a problem with your computer. They request remote access to your computer and will inevitably ask for your credit card details. This scam can result in your credit card being debited for hundreds of Euros.
The typical ‘Microsoft Support Scam’ usually plays out like this:
My computer was acting really slow. I then received a phone call from someone purporting to be from Microsoft Technical Support who claimed they had detected a problem on my PC. They then instructed me to navigate to the Event Viewer in Windows. They claimed that the error messages displaying there were serious and were causing my PC to be slow. I was requested to download software which gave them access to my computer. They demanded hundreds of Euros to fix it and demanded my credit card details. I refused to pay and he got very aggressive.
The type of scenario above is typical of this scam. Over the years, we have seen many users from doctors to company CEOs fall for it. There are a number of reasons why it works. Firstly, it uses the power of coincidence. Most people at one stage or another find that their PC becomes slow. So some users simply think that Microsoft is being proactive in their support when the call arrives. When users are instructed to go to the Event Viewer on their PC and see yellow warning triangles, they become convinced there is a serious issue. (In reality, these yellow warning triangles will show up even on a perfectly healthy PC, as they normally relate to small issues, such as a printer being offline or the system momentarily being unable to connect to the internet). Moreover, the victim can usually hear the hubbub of a busy call centre in the background, not realising that it’s really the sound of other victims getting scammed!
Do they still have access to my PC and what other precautions should I take after this incident?
It is advisable to cancel all the credit cards that the scammers have details of. From our experience, the perpetrators of this scam use different remote login applications to access your PC. Make sure that all of these are totally removed from your system. It is advisable that you get your Windows or Mac system fully checked out by a technician who has experience in dealing with hacked computers.
Can Apple Macs be hacked?
There is a misconception out there that Macs can’t be hacked. But this belief imbues Mac users with a dangerous sense of false security. In the threat environment of today, a substantial number of attacks are based on what is known as social engineering. This means that instead of attackers trying to exploit a technical weakness in the software or hardware of a system, they will try to exploit the user instead. For example, a hacker can gain remote access to your Mac via a phishing attack in which the user inadvertently installs malware or remote access software onto your Mac. It is much easier to get the user to install the malware than for the hacker to break in and do it themselves. Once the data-stealing malware or remote access software is installed, they can access your Keychain, capture your passwords and steal data.

My Gmail account has been hacked, can you help?
For a substantial number of Irish computer users (both personal and business), Gmail is their main email account. Discovering that it has been hacked is not a pleasant feeling. Once hackers have access to it, they can steal data, delete data, send spam and phishing emails from it, redirect emails to their own email account and impersonate you when engaging in illegal transactions.
We can:
- Help you re-secure your Gmail account to prevent future unauthorised access.
- Examine your Windows or Mac system for evidence of malware such as keyloggers, trojans and web-cam hijackers.
- Help determine how a hacker accessed your account.
- Examine all your Gmail account settings for any evidence of forwarding or redirect rules or any other anomalous settings set-up by a hacker.
- Recover emails which have been recently deleted.
Please Note: Unfortunately, we cannot help you if you have lost access to Gmail account.
I think my (Eir, Virgin Media, Vodafone, Tp-Link, Zyxel) router has been hacked. All computers and phones in my house keep on redirecting to specific websites that do not look very trustworthy.
It sounds like your router has been hijacked. Do not attempt to enter any confidential information to any websites as it may be of risk of being compromised.
Why didn’t my anti-virus or anti-malware software prevent my computer from being hacked?
Using anti-virus or anti-malware software on your system is not a panacea. Most anti-virus packages only have 70%-80% virus or malware detection rates, at best. This is because anti-virus packages still primarily use signature-based scanning and the virus/malware authors are always one step ahead. The design viruses are polymorphic and mutate once inside your system, making them harder to detect and eradicate. Moreover, an increasingly large number of malware strains are encrypted. This means they are undetectable when scanned by your computer security software. They only get activated once inside your system.
How do I prevent my computer from getting hacked in the future?
Open up any email attachments or weblinks with extreme prudence. In a lot of cases, innocent looking MS Office attachments, such as .doc and .xls carry infectious macros. Other dangerous attachments include .bat, .com, .cmd, .cpl, .chm, .js, .jse, .msp, .mst,.paf, .psc1 .zip, .rar, .scr, .vbs and .wsf. Even the savviest computer users can get caught by a phishing email. Unfortunately, checking email is now a perfunctory task that most people perform on autopilot. Try to develop the habit of stopping and thinking for 10-15 seconds before opening up any attachment or link sent via email. If in any doubt, contact the sender through another channel, such as telephone or SMS.
Do not be tempted to download random software applications for your phone or computer. Every piece of software that you install on your devices increases the attack surface. Even a seemingly benign weather app or game downloaded from the wrong source can be a conduit for nasty data-stealing malware. If you are downloading software, try to download it directly from source and not a third-party site such as Softonic or download.com.
Update to the latest version of your computer’s operating system. There are now almost weekly updates for Windows 10 and Apple’s OS X. You should NOT be using Windows 8, 7 or XP or vintage versions of OS X.
Update the operating system on your phone and the apps. Remove any non-essential apps.
Use complex and unique passwords on all your accounts. The name of your pet or favourite football team does not constitute a secure password. For example, using ‘casper’ alone is not secure. It takes about one second to crack. But a complex password like ‘casperfieldsmart!’ would take years to crack using standard computing power.
Make sure that you’re using the latest version of your internet browser (Edge, Chrome, Safari or Firefox). Remove all unwanted plugins.
Make sure that all your browser plugins, such as Adobe Reader and Java, are up-to-date.
Enable two-factor authentication(2FA) for any email and cloud services you are subscribed to.
Make sure that your wireless network is using at least WPA2 encryption and is secured by a complex password and not the name of your pet! It should not be using the default username and password. The firmware of the device should be updated to the latest version.
Never store passwords in plaintext on your computer or in the cloud. They should always be stored in an encrypted format.
Use a remote access VPN when accessing public Wi-Fi networks. This encrypts your data and prevents logins and passwords from being ‘sniffed’.
Be careful when entering your credit card details online. Many users erroneously believe that a website with a ‘padlock’ icon or HTTPS in the URL is sure to be a secure site. This could not be further from the truth. The padlock icon or HTTPS prefix just means that your connection to the website is secure. It does not mean that the information you enter into the site is going to be secure.
Always make sure you have current ‘offline’ backups of your data. Cryptoviruses can propagate from an infected system across a LAN (network) to other systems and storage devices in a matter of seconds. Always make sure that external storage devices, such as USB drives or NAS devices, are isolated from your network and only connected when a backup is scheduled to run.
Encrypt your data with an application such as Axcrypt. Or, if using Mac, use password protected folders for storing confidential data. This means even if a hacker does infiltrate your system, they still will have not access to your data.
Have you been hacked? Want to prevent this from happening ever again?
More than 80% of hacking incidents can now be attributed to human error. Cyber security awareness training is a proven way to prevent cyber-attacks or hacking incidents. We can recommend SecureClick who offer customised individual, group and organisational cyber security awareness training throughout Ireland.
Computer Ambulance are based in Dublin, Ireland. We offer a call-out service for most of the Dublin area. We also offer a secure remote technical support service to assist victims of hacking. Contact us on 353 1 685 4838.





